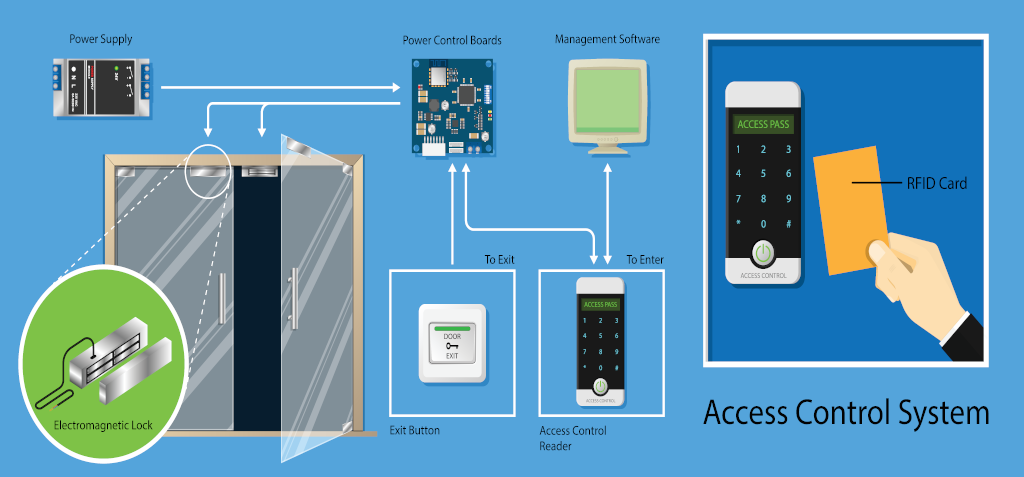
Access point:
The entrance point which can include security gates, turnstiles and door locks. A building can have a single access point, or multiple including meeting rooms, offices or any room that houses valuable or confidential items.
Credentials:
Credentials can include fobs and key card entry systems, encrypted badges, mobile credentials, PIN codes and passwords.
Readers and/or keypads:
At the access point, readers send the credential data to a control panel to authenticate the credential and request access. If using a keypad or biometric reader (such a fingerprint scan, facial ID, or retina scan), users will enter their PIN or complete a scan prior to obtaining access.
Control panel:
The control panel receives data from the reader and verifies the validity of the credential. If approved, the control panel transmits to the access point via the access control server, and the door will unlock. If the data is not approved, the user will be denied entry.
Access control server:
The server retains user data, access privileges, and audit logs. The server might be on-premises or managed in the cloud. The threat from hacking and security breaches requires that system maintenance and software updates be performed regularly.