Blog
Happy 4th of July
On this Independence Day 2021, we want to share our genuine appreciation to our Customers and Partners.
So, we at netRelevance wish you and yours a safe and happy 4th of July
moreA Safe Return To The Workplace
As COVID restrictions start to ease, businesses are faced with the challenge of providing their employees a safe return to the office. From a hybrid workplace model to monitoring building occupancy, flexibility and support may very well be the key to a successful return to the workplace.
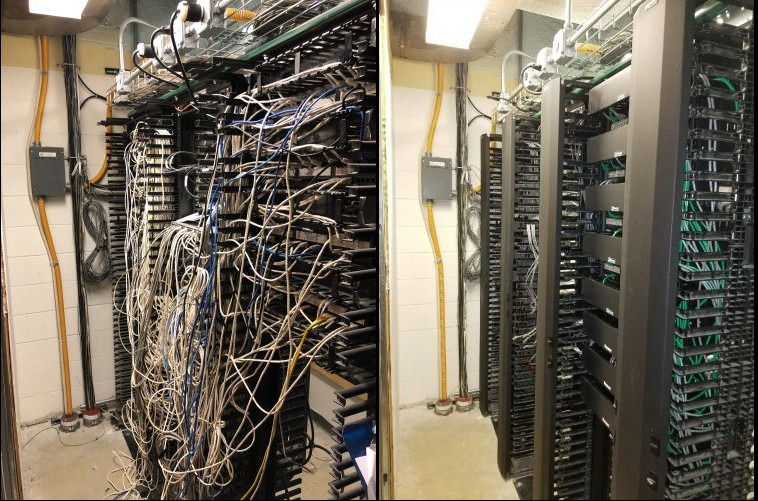
moreIT Closet Cleanup Guide
The cleanup of an IT closet can be quite cumbersome; therefore, you may be asking yourself where do I start?
moreDoes your network closet need a Spring Cleaning?
Spring is a time for renewal, growth and expansion. We see evidence of it all around us. For example, the blooming flowers and the return of leaves to our barren trees, remind us that this is the opportunity to start anew. In most of us, this encourages us to do a little Spring cleaning.
moreHappy Thanksgiving
On this Thanksgiving 2020, we want to share our genuine appreciation to our Customers and Partners.
So, we at netRelevance wish you and yours the blessings of Thanksgiving.
May you stay happy, healthy and safe this holiday and every day.
moreWhat is an IP Surveillance System?
VIDEO SURVEILLANCE PROVIDES PROTECTION AND PEACE OF MIND.
A reliable video surveillance system is important for any business. Protecting your assets helps protect your profits. Video surveillance goes by many names, including but not limited to, CCTV, security cameras, network video, video management systems and IP surveillance system.
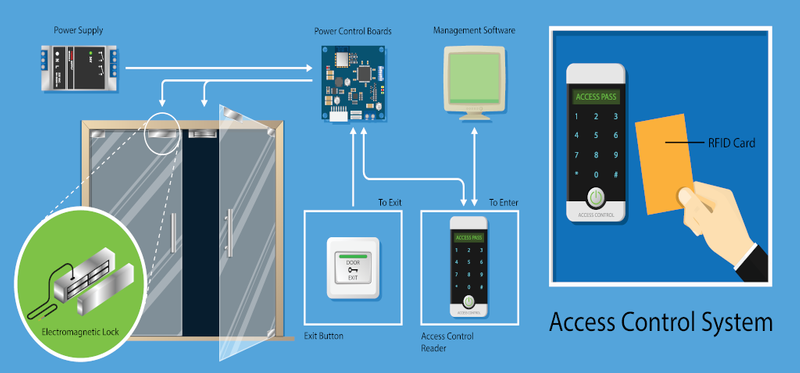
moreWhat is access control?
Access Control Basics
Access control systems are a type of physical security which allow you to restrict or allow access to a building or a specific area within a building. Usually, they are installed to protect businesses and property from vandalism, theft, and trespassing. For example, they are especially useful in facilities that require higher security and protection. Therefore, physical barriers, like retaining walls, fences, etc. can be effective, but access control allow you to control how and when a person can gain entry.
moreConnect PVM’s during COVID-19
It’s both digital signage and an active theft deterrent seamlessly integrated into a single device.
Traditionally, Public View Monitors (PVM) reside in high-value, high-visibility locations with a focus on security. Now you can re-purpose that space by adding digital signage, without comprising the theft deterrent already in place. Clinton electronics Connect PVM’s and Axis cameras can work together with digital messaging. This can work as a reminder of mask mandates and proper social distancing.
more